In today’s digitally connected world, our lives are increasingly intertwined with the internet. From banking and shopping to communication and entertainment, almost every aspect of our daily routines relies on online platforms. While this interconnectedness brings countless benefits, it also exposes us to a growing number of cyber threats. Data breaches, phishing scams, malware attacks, and identity theft are becoming increasingly common, making cybersecurity a critical concern for everyone.
Staying safe in the digital world is no longer an option but a necessity. It’s not just about protecting your sensitive information; it’s about safeguarding your privacy, financial security, and even your physical well-being. This comprehensive guide will equip you with the knowledge and practical tips you need to navigate the digital landscape safely and confidently. We’ll cover essential cybersecurity best practices for individuals, families, and businesses, ensuring that you understand the threats, implement robust defenses, and stay one step ahead of cybercriminals.
Understanding the Importance of Cybersecurity

In today’s digital world, our lives are increasingly intertwined with technology. We bank online, shop online, communicate online, and even work online. This digital dependency brings about a new set of risks, making cybersecurity a crucial aspect of our lives.
Cybersecurity is the practice of protecting computer systems and networks from unauthorized access, use, disclosure, disruption, modification, or destruction. It is essential because it safeguards our personal information, financial data, and even our physical safety.
The consequences of a cybersecurity breach can be devastating. From identity theft and financial fraud to data leaks and system downtime, the ramifications can be far-reaching and costly. Understanding the importance of cybersecurity means recognizing the potential dangers and taking proactive steps to mitigate them.
By implementing strong passwords, being cautious of phishing attempts, and keeping software up-to-date, we can significantly enhance our online security. It’s a collective responsibility to stay informed and vigilant in navigating the digital landscape.
Creating Strong and Unique Passwords
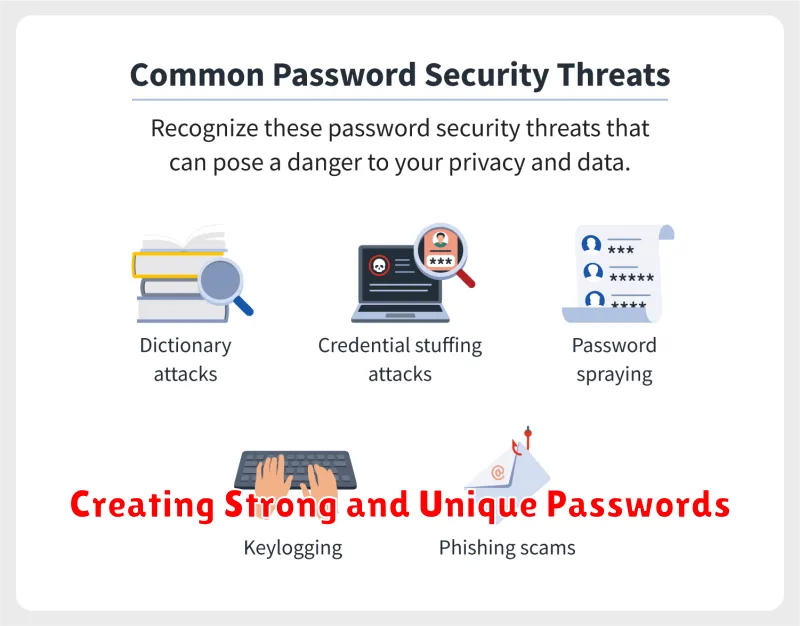
In today’s digital world, our data is constantly under threat. From phishing scams to data breaches, protecting our online information is more crucial than ever. One of the most important steps in safeguarding your digital life is creating strong and unique passwords.
Strong passwords are not easily guessed and are difficult to crack. They should be at least 12 characters long, including a combination of uppercase and lowercase letters, numbers, and symbols.
Unique passwords mean using a different password for every online account. This way, even if one account is compromised, the attacker won’t have access to your other accounts.
Here are some tips for creating strong and unique passwords:
- Avoid using common words or personal information like your name, birthday, or pet’s name.
- Use a password manager to generate and store your passwords securely.
- Enable two-factor authentication whenever possible.
- Change your passwords regularly, at least every 90 days.
By following these tips, you can significantly reduce the risk of your accounts being compromised and keep your personal information safe.
Enabling Two-Factor Authentication for Enhanced Security
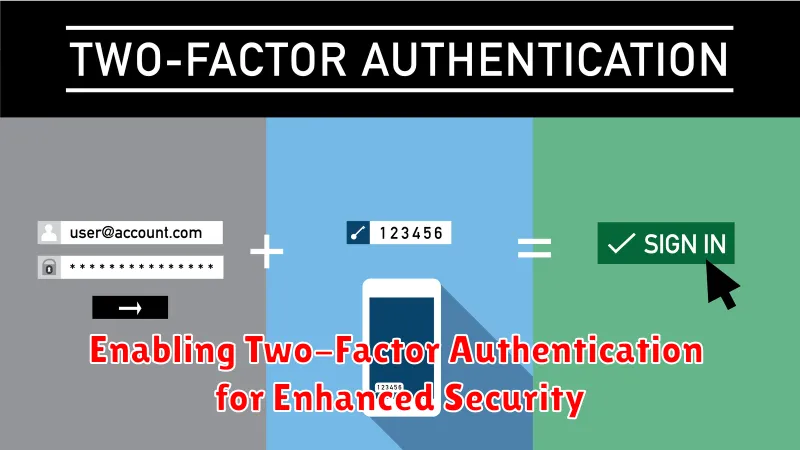
In today’s digital landscape, safeguarding your online accounts is paramount. One of the most effective ways to bolster your security is by enabling two-factor authentication (2FA). This simple yet powerful measure adds an extra layer of protection, making it significantly harder for unauthorized individuals to access your accounts.
How does it work? When you enable 2FA, you’ll be prompted to enter a unique code in addition to your password when logging in. These codes are typically generated through an authenticator app on your smartphone, a physical security key, or sent to your registered email address or phone number.
The beauty of 2FA lies in its ability to thwart even if your password is compromised. Even if someone manages to obtain your password, they’ll still need access to your phone or security key to generate the second factor code, rendering their attempt to log in unsuccessful.
Enabling 2FA is a simple yet impactful step you can take to safeguard your digital assets. Whether you’re using online banking, social media platforms, email accounts, or any other service that offers 2FA, make it a priority. You’ll gain peace of mind knowing that your accounts are protected by an extra layer of security.
Recognizing and Avoiding Phishing Attacks
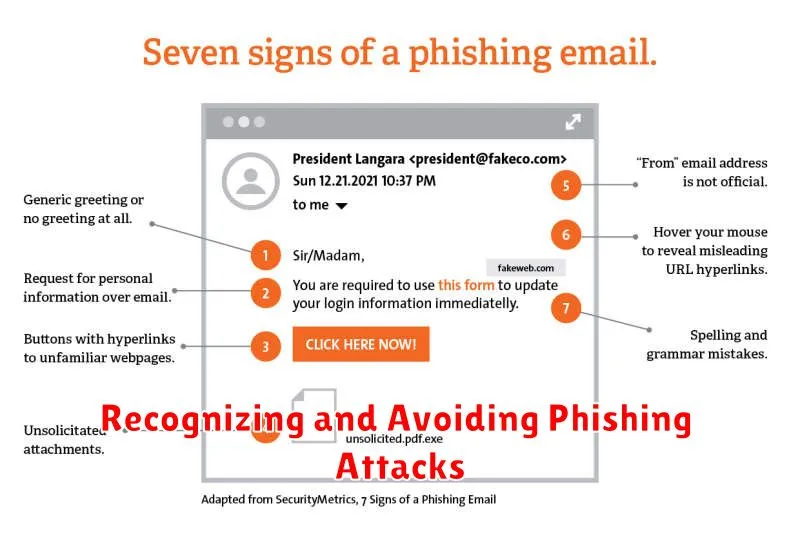
In today’s digital world, where we rely heavily on the internet for everything from banking to communication, it’s essential to be aware of the threats lurking online. One of the most common and dangerous threats is phishing, a type of cyberattack designed to steal your personal information, such as passwords, credit card details, and even your identity.
Phishing attacks often come disguised as legitimate emails, messages, or websites. They might appear to be from a trusted source, like your bank, a social media platform, or a government agency. The goal of these attacks is to trick you into clicking on a malicious link, downloading a harmful file, or providing your sensitive information.
Recognizing Phishing Attempts
Here are some key indicators that can help you identify phishing attacks:
- Suspicious URLs: Look for typos, unusual characters, or domain names that don’t match the sender’s organization. Hover over the link before clicking to see the actual URL.
- Urgent or Threatening Language: Phishing emails often use fear-mongering tactics, demanding immediate action or threatening consequences if you don’t comply. Be cautious of messages that make you feel pressured or anxious.
- Grammatical Errors and Poor Formatting: Legitimate organizations generally have well-written and professionally designed communications. Watch for typos, spelling errors, and inconsistent formatting, which are common red flags.
- Requesting Sensitive Information: Be wary of any communication that asks for your password, credit card details, social security number, or other personal information over email, text, or phone. Legitimate organizations will never request this information through such channels.
Avoiding Phishing Attacks
Here are some practical steps you can take to protect yourself from phishing attacks:
- Be Skeptical: Always be cautious when opening emails or clicking on links, even if they appear to be from a familiar source. Verify the sender’s identity and the content of the message.
- Enable Two-Factor Authentication: This extra layer of security requires you to enter a code sent to your phone in addition to your password, making it much harder for attackers to gain access to your accounts.
- Keep Your Software Updated: Regularly update your operating system, antivirus software, and other applications to patch security vulnerabilities that attackers could exploit.
- Use Strong Passwords: Choose complex passwords that are difficult to guess and avoid using the same password for multiple accounts.
- Be Aware of Social Engineering: Phishing attacks can also use social engineering tactics, such as impersonating a friend or colleague to gain your trust. Be cautious of requests for personal information from people you don’t know or trust.
By staying vigilant and adopting these simple practices, you can significantly reduce your risk of falling victim to phishing attacks and keep your personal information safe in the digital world.
Keeping Software Up-to-Date with Latest Security Patches

In today’s digital world, keeping our devices and software secure is more important than ever. Cybercriminals are constantly developing new ways to exploit vulnerabilities in our systems, so it’s crucial to stay one step ahead by installing the latest security patches. These updates are essential for patching known security holes and preventing attackers from gaining access to our sensitive information.
Think of security patches as a shield for your device. They are like armor that protects your system from attacks. When you don’t install updates, you’re essentially leaving your defenses down, making your device an easy target for hackers.
Here’s why updating your software is vital:
- Fixes vulnerabilities: Security patches address known weaknesses in software that can be exploited by attackers. By installing updates, you’re closing these loopholes and making your system more secure.
- Prevents malware infection: Many security patches target vulnerabilities that attackers use to install malware, such as viruses and ransomware. Updating your software significantly reduces your risk of infection.
- Improves performance: While not always the primary focus, updates often include performance enhancements and bug fixes, leading to a smoother and more efficient experience.
To ensure you’re always protected, make sure to enable automatic updates for all your devices and software. This will ensure you receive the latest security patches as soon as they become available. You can also check for updates manually at regular intervals. Additionally, consider using a reputable antivirus program to provide an extra layer of protection.
By keeping your software up-to-date, you’re taking a proactive approach to cybersecurity and significantly reducing your risk of becoming a victim of cyberattacks. Remember, in the digital world, staying safe starts with keeping your software secure.
Securing Your Home Network with Strong Wi-Fi Passwords
In today’s digital age, our homes are increasingly connected to the internet, making it more important than ever to secure our home networks. One of the most crucial aspects of home network security is using strong Wi-Fi passwords. A weak password can leave your network vulnerable to unauthorized access, putting your personal information and devices at risk.
Here are some tips for creating strong Wi-Fi passwords:
- Length: Aim for a password that is at least 12 characters long.
- Complexity: Include a combination of uppercase and lowercase letters, numbers, and symbols.
- Avoid common phrases: Don’t use common words, names, or dates that could be easily guessed.
- Don’t reuse passwords: Use unique passwords for your Wi-Fi network and other online accounts.
Once you’ve created a strong password, it’s essential to protect it. Don’t share your Wi-Fi password with anyone you don’t trust. Avoid writing it down where it can be easily found. If you need to share your password with a guest, consider creating a temporary guest network with a separate, weaker password.
By taking these simple steps, you can significantly enhance the security of your home network and protect your personal information from unauthorized access.
Protecting Your Privacy on Social Media Platforms
Social media has become an integral part of our lives, connecting us with friends, family, and the world. However, it comes with its own set of risks, especially concerning our privacy. It’s crucial to be aware of these risks and take proactive steps to protect ourselves. Here’s a guide to safeguarding your privacy on social media platforms.
Be Mindful of What You Share: Think twice before posting personal information such as your address, phone number, or financial details. Remember that once something is online, it can be difficult to remove completely. Consider using privacy settings to limit who can see your posts.
Review Privacy Settings: Most social media platforms offer privacy settings that allow you to control who can see your information. Take time to understand these settings and adjust them according to your comfort level. Choose the strictest settings possible to protect your data.
Be Wary of Third-Party Apps: Many apps require access to your social media account information. Carefully review the permissions requested and only grant access if necessary. Be cautious about apps that seem suspicious or ask for excessive permissions.
Use Strong Passwords: Create unique and strong passwords for each of your social media accounts. Avoid using common passwords or personal information. Consider using a password manager to securely store your passwords.
Be Aware of Scams and Phishing: Social media is a common target for scammers and phishing attacks. Be wary of suspicious messages or links, and never share personal information with strangers. If you’re unsure about a message, it’s always best to err on the side of caution and report it to the platform.
Protecting your privacy on social media platforms requires vigilance and awareness. By following these tips, you can navigate the digital world with greater confidence and safeguard your personal information.
Backing Up Important Data Regularly

In today’s digital world, our data is more important than ever. It holds our memories, our work, and even our financial information. That’s why it’s crucial to back up your data regularly. This protects you from data loss due to accidental deletion, hardware failure, or even cyberattacks.
There are many different ways to back up your data. You can use an external hard drive, a cloud storage service, or even a combination of both. No matter which method you choose, make sure to back up your data frequently, ideally on a daily or weekly basis.
Here are some additional tips for backing up your data:
- Back up to multiple locations. This helps ensure that your data is safe even if one of your backup locations is compromised.
- Use a reliable backup service. Choose a service that is known for its security and reliability.
- Test your backups regularly. This ensures that your backups are working properly and that you can restore your data if needed.
Backing up your data is a crucial part of protecting yourself in the digital world. By following these tips, you can help ensure that your data is safe and secure.
Using a Virtual Private Network (VPN) for Secure Browsing

In today’s digital age, where we conduct most of our activities online, cybersecurity is paramount. One effective tool to enhance your online security is a Virtual Private Network (VPN). A VPN creates a secure and encrypted connection between your device and the internet, masking your IP address and encrypting your data. This makes it difficult for hackers and snoopers to intercept your online activity.
Here’s how a VPN works: When you connect to a VPN server, your internet traffic is routed through that server, effectively concealing your real IP address. This makes it challenging for websites and advertisers to track your browsing history or identify your location. Additionally, the encryption process adds an extra layer of security, making it much harder for unauthorized parties to access your data.
Using a VPN offers several benefits for secure browsing:
- Privacy Protection: By masking your IP address, a VPN protects your online privacy, preventing websites and advertisers from tracking your activity.
- Secure Public Wi-Fi: When connecting to public Wi-Fi networks, which can be vulnerable to security breaches, a VPN encrypts your data, making it safer to use.
- Bypass Geo-restrictions: Some websites and services restrict access based on your geographical location. A VPN allows you to access content from other regions by connecting to a server in that location.
- Enhanced Security: The encryption provided by a VPN makes it more difficult for hackers to intercept your data, particularly when using public Wi-Fi networks or accessing sensitive websites.
When choosing a VPN, it’s essential to consider factors such as speed, security protocols, server locations, and pricing. Look for a reputable VPN provider with strong encryption, a no-logs policy, and positive user reviews.
By incorporating a VPN into your cybersecurity strategy, you can significantly enhance your online security and enjoy a more secure and private browsing experience.
Being Cautious of Suspicious Links and Downloads

In the digital age, we’re constantly bombarded with information and opportunities. From emails to social media messages, it can be easy to click on a link or download a file without thinking twice. However, this can be a risky move, as malicious actors often use these tactics to spread malware and steal your personal information. That’s why it’s crucial to be cautious of suspicious links and downloads and take the necessary steps to protect yourself.
Here are a few key things to keep in mind:
- Think before you click: Before clicking on a link, ask yourself if it seems legitimate. Is it from a trusted source? Does the link make sense in the context of the message you received? If you have any doubts, don’t click.
- Hover over links: Most browsers allow you to hover your mouse over a link to see the full URL before clicking. This can help you identify any red flags, such as misspelled words or suspicious domains.
- Beware of attachments: Be wary of email attachments, especially if they’re from unknown senders or if the file type is unexpected. Never open an attachment if you’re not sure what it is or if the sender seems suspicious.
- Don’t download from untrusted sources: Only download software and apps from reputable sources, like official websites and app stores. Be cautious about downloading files from torrent sites or other unofficial channels, as these can contain malware.
- Keep your software updated: Software updates often include security patches that fix vulnerabilities, making it harder for hackers to exploit them. Make sure your operating system, antivirus software, and other applications are up to date.
By being vigilant and following these simple tips, you can significantly reduce your risk of falling victim to malicious links and downloads. Remember, a little caution goes a long way in keeping your online safety and privacy secure.
Educating Yourself and Others about Cybersecurity Threats

In today’s digital landscape, cybersecurity is no longer a niche concern; it’s a vital aspect of everyday life. From online banking to social media interactions, our data is constantly at risk, making it essential to stay informed about common threats. Understanding these threats empowers us to take proactive steps to protect ourselves and others.
One of the most common cybersecurity threats is phishing, where attackers attempt to trick individuals into revealing sensitive information like passwords or credit card details. This can be done through emails, text messages, or even social media posts that appear legitimate but are actually designed to deceive.
Another threat is malware, which refers to malicious software that can infect your devices and steal your data, monitor your online activity, or even take control of your computer. Malware can be spread through downloads, infected websites, or even email attachments.
Ransomware is a particularly dangerous type of malware that encrypts your files and demands payment to restore access. This can be devastating for individuals and businesses alike.
Beyond these common threats, there’s a constant evolution of cyberattacks, making it crucial to stay updated on the latest trends and vulnerabilities. By staying informed, we can better identify and avoid potential risks.
Educating ourselves about cybersecurity threats is essential for everyone. By sharing knowledge and raising awareness, we can create a safer digital environment for all.