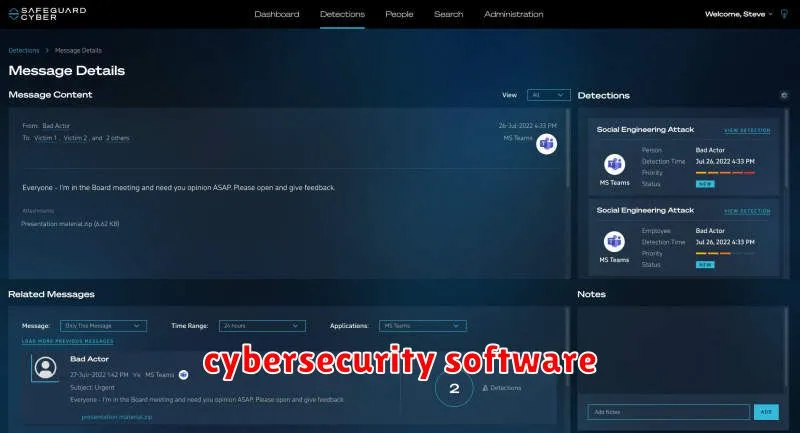
In the ever-evolving digital landscape, where cyber threats are becoming increasingly sophisticated, cybersecurity remains a top priority for individuals and organizations alike. As we step into 2024, the need for robust security solutions is more critical than ever. From data breaches to ransomware attacks, the potential consequences of cyberattacks are far-reaching, impacting everything from financial stability to reputational integrity. This article will delve into the top software solutions that can bolster your cybersecurity posture and provide enhanced protection against emerging threats.
With the advent of new technologies like artificial intelligence (AI) and the Internet of Things (IoT), the attack surface continues to expand, creating new vulnerabilities for hackers to exploit. To stay ahead of the curve, it is essential to invest in comprehensive cybersecurity solutions that incorporate cutting-edge technologies and best practices. This includes implementing robust firewalls, intrusion detection and prevention systems (IDS/IPS), and advanced endpoint security to safeguard your digital assets. By understanding the latest cybersecurity trends and adopting the right software solutions, you can effectively mitigate risks and ensure the security of your sensitive information in 2024.
The Evolving Threat Landscape: Cybersecurity Challenges in 2024
The cybersecurity landscape is constantly shifting, with new threats emerging and attackers becoming more sophisticated. As we enter 2024, organizations face a growing range of challenges, driven by factors such as:
Increased reliance on cloud computing: Cloud adoption has created new attack surfaces, making it crucial to secure data and applications in the cloud. Organizations need to ensure they have robust cloud security measures in place, including access control, data encryption, and threat detection.
The rise of AI-powered attacks: Artificial intelligence (AI) is being used by both attackers and defenders. While AI can enhance security efforts, it also empowers attackers to automate attacks, making them more targeted and difficult to detect.
Growing use of IoT devices: The Internet of Things (IoT) is expanding rapidly, creating a vast network of connected devices. Many of these devices lack robust security measures, making them vulnerable to attacks.
The proliferation of ransomware: Ransomware attacks are becoming more common and sophisticated, with attackers demanding larger ransoms and exploiting vulnerabilities to gain access to sensitive data. Organizations need to implement strong security measures to prevent ransomware attacks, including regular backups and endpoint protection.
Evolving cybercrime tactics: Attackers are constantly evolving their tactics, using new techniques such as social engineering, phishing, and malware to compromise systems. Organizations need to stay informed about the latest threats and adopt proactive security measures to mitigate these risks.
Essential Cybersecurity Software Categories for 2024
As we navigate the ever-evolving digital landscape in 2024, robust cybersecurity is no longer a luxury but a necessity. The increasing sophistication of cyberattacks demands a comprehensive and proactive approach. To effectively combat these threats, organizations must leverage the power of specialized cybersecurity software solutions. This article delves into essential cybersecurity software categories that are critical for enhanced protection in 2024.
Endpoint Security
Endpoint security software plays a vital role in safeguarding individual devices, such as laptops, desktops, and mobile phones, against malware and other threats. These solutions offer comprehensive protection by incorporating features like antivirus, anti-malware, firewalls, and intrusion detection systems. By deploying endpoint security, organizations can ensure the integrity and confidentiality of sensitive data stored and processed on endpoints.
Network Security
Network security software is designed to protect an organization’s network infrastructure from unauthorized access, data breaches, and other cyber threats. This category encompasses solutions like firewalls, intrusion detection and prevention systems (IDS/IPS), VPNs, and network segmentation tools. Implementing robust network security measures is crucial for safeguarding sensitive data, ensuring business continuity, and maintaining compliance with relevant regulations.
Data Security and Privacy
In today’s data-driven world, data security and privacy are paramount. Organizations must employ specialized software to protect sensitive information from unauthorized access, use, or disclosure. This category includes data loss prevention (DLP) solutions, data encryption tools, and privacy management platforms. By adopting data security and privacy software, businesses can maintain compliance with regulations like GDPR and CCPA, build trust with customers, and protect their reputation.
Security Information and Event Management (SIEM)
SIEM solutions are essential for centralized security monitoring and incident response. By aggregating security data from various sources, SIEM tools provide a comprehensive view of potential threats and security events. This allows security teams to detect anomalies, investigate incidents, and respond effectively to threats. SIEM software empowers organizations to proactively mitigate risks and ensure a rapid and efficient response to security incidents.
Vulnerability Management
Vulnerability management software is crucial for identifying and mitigating security vulnerabilities within an organization’s IT infrastructure. By scanning systems for known weaknesses, these solutions enable security teams to prioritize patches, updates, and remediation efforts. Vulnerability management software plays a critical role in reducing the attack surface and minimizing the impact of potential cyberattacks.
Investing in these essential cybersecurity software categories is a crucial step towards building a robust and resilient defense against evolving cyber threats. By adopting the right software solutions, organizations can safeguard their valuable assets, ensure business continuity, and maintain a competitive edge in the digital landscape.
Next-Generation Antivirus and Endpoint Protection: Staying Ahead of Threats
As the landscape of cyber threats continues to evolve, traditional antivirus solutions are no longer sufficient. Modern attackers leverage sophisticated techniques to bypass traditional defenses, making it crucial for organizations to adopt next-generation antivirus (NGAV) and endpoint protection (EPP) solutions. These advanced technologies offer comprehensive protection against the latest threats, empowering businesses to stay ahead of the curve.
NGAV goes beyond signature-based detection by employing machine learning and behavioral analysis to identify and neutralize unknown threats. It proactively analyzes suspicious activities, blocking malicious code before it can execute. EPP provides a layered approach to endpoint security, encompassing a range of features such as vulnerability assessment, device control, and data loss prevention. By combining these capabilities, NGAV and EPP create a robust security posture that safeguards sensitive data and critical systems.
Here are some key advantages of adopting NGAV and EPP:
- Enhanced Threat Detection: NGAV utilizes advanced techniques to detect and neutralize even zero-day threats, which are previously unknown attacks that haven’t been identified by traditional antivirus solutions.
- Improved Performance: NGAV solutions are optimized for minimal impact on system performance, ensuring a smooth user experience.
- Real-Time Protection: NGAV and EPP provide real-time protection, continuously monitoring endpoints for suspicious activity and blocking threats before they can cause harm.
- Centralized Management: NGAV and EPP solutions offer centralized management consoles, allowing security teams to easily configure policies, monitor threats, and deploy updates across the entire network.
By investing in NGAV and EPP solutions, organizations can bolster their cybersecurity posture and safeguard their valuable assets. As the threat landscape continues to evolve, staying ahead of the game requires embracing cutting-edge technologies that provide comprehensive endpoint protection.
Firewalls and Intrusion Detection Systems: Building Strong Defenses
In the ever-evolving landscape of cybersecurity, robust defenses are paramount. Firewalls and intrusion detection systems (IDS) are crucial components of a comprehensive security strategy, acting as vigilant guardians against malicious threats.
Firewalls function as digital gatekeepers, meticulously inspecting incoming and outgoing network traffic. By establishing strict rules, they block unauthorized access and prevent malicious actors from penetrating your network. Network firewalls monitor traffic at the network level, while host-based firewalls safeguard individual devices. These tireless protectors analyze data packets, filtering out suspicious activity and safeguarding your valuable data.
Intrusion detection systems (IDS), on the other hand, act as vigilant watchdogs, continuously monitoring network activity for suspicious patterns. They analyze data streams, identifying potential threats and alerting administrators to suspicious behavior. Network-based IDS monitor traffic across the entire network, while host-based IDS focus on individual devices. These watchful eyes can detect a wide range of threats, including malware, unauthorized access attempts, and denial-of-service attacks, enabling swift action to mitigate potential harm.
The synergy between firewalls and IDS creates a powerful defense mechanism. Firewalls serve as the first line of defense, blocking known threats, while IDS act as a secondary layer, identifying and alerting against emerging threats. This layered approach provides a comprehensive shield against a multitude of cyberattacks, safeguarding your digital assets and ensuring the integrity of your operations.
By strategically deploying firewalls and IDS, organizations can significantly bolster their cybersecurity posture. These powerful tools act as vigilant guardians, safeguarding networks and data from malicious threats. By embracing these essential technologies, you can build a robust defense, mitigating risk and ensuring a secure digital future.
Data Loss Prevention (DLP) and Encryption Software: Safeguarding Sensitive Information
In today’s digital landscape, safeguarding sensitive information is paramount. Data breaches and cyberattacks pose a significant threat to individuals and organizations alike. Data loss prevention (DLP) and encryption software are two essential tools in the cybersecurity arsenal, working in tandem to protect critical data from unauthorized access and loss.
DLP software acts as a vigilant guardian, monitoring data flows within and outside the organization. It identifies and prevents sensitive information from leaving the controlled environment through various channels, including email, instant messaging, and cloud storage. By setting predefined rules, DLP solutions can detect and block unauthorized data transfers, ensuring that confidential information remains secure.
While DLP safeguards data in transit, encryption software adds an extra layer of protection by transforming data into an unreadable format. This process ensures that even if data falls into the wrong hands, it remains inaccessible without the proper decryption key. Encryption can be applied to various data formats, including files, databases, and communications, making it a robust defense against data breaches.
The combined power of DLP and encryption software creates a formidable barrier against data loss and unauthorized access. They work synergistically, providing comprehensive protection at multiple levels. DLP prevents the leakage of sensitive information, while encryption ensures that even if data is intercepted, it remains secure and unusable without the appropriate decryption key.
Organizations of all sizes should prioritize the implementation of DLP and encryption solutions to enhance their cybersecurity posture. These software solutions are essential in today’s data-driven world, providing peace of mind and safeguarding valuable assets from the ever-growing threat of cyberattacks.
Security Information and Event Management (SIEM): Centralized Threat Monitoring
In the dynamic landscape of cybersecurity, organizations face an ever-growing challenge in effectively monitoring and responding to threats. Security Information and Event Management (SIEM) solutions play a crucial role in tackling this challenge by providing centralized threat monitoring capabilities.
SIEM systems act as a central hub for collecting and analyzing security data from various sources, including firewalls, intrusion detection systems (IDS), antivirus software, and logs from servers and applications. This data aggregation allows for comprehensive visibility into network activity, enabling security teams to identify potential threats and respond quickly.
A key strength of SIEM is its ability to detect anomalies and suspicious patterns in security data. By correlating events and analyzing user behavior, SIEM systems can identify potential attacks, such as unauthorized access attempts, data breaches, and malware infections. This real-time threat detection empowers security teams to take proactive steps to mitigate risks and prevent breaches.
Furthermore, SIEM solutions offer robust incident response capabilities. When a threat is detected, SIEM systems provide detailed information on the attack, enabling security teams to quickly understand the situation and respond accordingly. This includes isolating affected systems, containing the spread of malware, and initiating incident investigation and remediation processes.
In conclusion, Security Information and Event Management (SIEM) solutions are essential for centralized threat monitoring in today’s cybersecurity landscape. By aggregating security data, detecting anomalies, and providing incident response capabilities, SIEM systems empower organizations to stay ahead of threats, protect their sensitive information, and maintain business continuity.
Vulnerability Management Solutions: Proactive Security Posture
In the ever-evolving landscape of cybersecurity, staying ahead of threats is paramount. Vulnerability management plays a critical role in achieving this goal by identifying, prioritizing, and mitigating potential weaknesses in your systems. Proactive vulnerability management empowers organizations to fortify their security posture, reducing the risk of costly breaches and data loss.
Vulnerability management solutions provide a comprehensive approach to identify and address vulnerabilities across your entire IT infrastructure. These solutions leverage advanced scanning technologies, threat intelligence feeds, and expert analysis to pinpoint potential entry points for attackers. By continuously monitoring for vulnerabilities and prioritizing remediation efforts, these tools help organizations stay one step ahead of the threat curve.
Key benefits of adopting vulnerability management solutions include:
- Reduced attack surface: By identifying and patching vulnerabilities promptly, organizations minimize the number of potential attack vectors.
- Improved security posture: Proactive vulnerability management strengthens overall security by addressing weaknesses before they can be exploited.
- Compliance adherence: Many industry regulations and standards require organizations to have robust vulnerability management programs in place.
- Cost savings: By preventing breaches, organizations avoid the financial and reputational damage associated with security incidents.
Choosing the right vulnerability management solution is essential. Consider factors such as your organization’s size, IT infrastructure complexity, budget, and specific security needs. Look for solutions that offer comprehensive scanning capabilities, automated remediation workflows, and robust reporting features.
By embracing vulnerability management solutions, organizations can establish a proactive security posture and protect themselves from the ever-increasing threat landscape. In today’s digital world, vulnerability management is not just a good practice; it is a necessity.
Cloud Security Posture Management (CSPM): Securing the Cloud
In today’s digital landscape, organizations are rapidly migrating to the cloud for its agility, scalability, and cost-effectiveness. However, this transition also presents new security challenges. As organizations move their workloads and data to the cloud, it’s crucial to ensure their cloud security posture is robust and continuously monitored. This is where Cloud Security Posture Management (CSPM) comes into play.
CSPM is a critical aspect of cloud security that focuses on maintaining the overall security posture of your cloud environment. It involves a set of tools and processes designed to assess, monitor, and remediate potential security risks across your cloud infrastructure. CSPM solutions help organizations gain visibility into their cloud deployments, identify security gaps, and enforce compliance with industry best practices and regulatory requirements.
Here are some key benefits of implementing a CSPM solution:
- Enhanced Visibility and Control: CSPM provides a comprehensive view of your cloud infrastructure, including resources, configurations, and user activity. This visibility allows you to identify potential vulnerabilities and misconfigurations before they can be exploited.
- Automated Risk Assessment and Remediation: CSPM solutions automate the process of identifying and prioritizing security risks. They can also automatically remediate certain vulnerabilities, reducing manual intervention and accelerating security response times.
- Improved Compliance: CSPM helps organizations meet compliance requirements by automatically assessing and monitoring their cloud infrastructure against relevant regulations, such as PCI DSS, HIPAA, and GDPR.
- Reduced Security Costs: By proactively identifying and addressing security vulnerabilities, CSPM solutions help prevent costly security breaches and data leaks.
As organizations continue to adopt cloud-based technologies, CSPM becomes increasingly essential. By implementing a robust CSPM solution, organizations can strengthen their cloud security posture, reduce their risk profile, and ensure their data and applications remain secure.
Identity and Access Management (IAM) Solutions: Controlling User Access
In today’s digital landscape, securing sensitive data and applications is paramount. Identity and Access Management (IAM) solutions play a crucial role in achieving this goal by establishing and enforcing policies that control user access to resources. IAM systems ensure that only authorized individuals can access the information and systems they need to perform their job functions, effectively minimizing the risk of unauthorized access and data breaches.
IAM solutions encompass a wide range of functionalities, including:
- User provisioning and deprovisioning: Automating the process of creating, managing, and deleting user accounts, ensuring that access is granted and revoked promptly.
- Authentication: Verifying user identities through multi-factor authentication (MFA) and other robust methods to prevent unauthorized logins.
- Authorization: Defining and enforcing access control policies, granting specific permissions to users based on their roles and responsibilities.
- Single sign-on (SSO): Enabling users to access multiple applications with a single set of credentials, streamlining the user experience while enhancing security.
- Password management: Providing secure password storage, enforcing strong password policies, and offering password reset functionalities.
By implementing a comprehensive IAM solution, organizations can significantly enhance their cybersecurity posture by:
- Reducing the risk of unauthorized access: IAM solutions enforce strict access control policies, ensuring that only authorized individuals can access sensitive data and systems.
- Improving compliance: IAM systems help organizations comply with industry regulations and data privacy laws, such as GDPR and HIPAA.
- Streamlining user administration: IAM solutions automate user management tasks, reducing administrative overhead and improving efficiency.
- Enhancing security awareness: By raising awareness of access control policies and implementing strong authentication methods, IAM systems promote a culture of security within the organization.
In conclusion, IAM solutions are essential for organizations seeking to strengthen their cybersecurity defenses in the face of evolving threats. By controlling user access to resources, IAM systems provide a critical layer of protection, ensuring the confidentiality, integrity, and availability of sensitive data.
Cybersecurity Awareness Training: Empowering Your Workforce
In the ever-evolving landscape of cybersecurity, a robust defense strategy requires more than just advanced software solutions. A crucial element is empowering your workforce with the knowledge and skills to navigate the digital world safely and responsibly. Cybersecurity awareness training plays a vital role in equipping your employees to identify and mitigate potential threats, safeguarding your organization from cyberattacks.
Effective cybersecurity awareness training programs go beyond simply delivering information. They engage employees through interactive exercises, realistic simulations, and practical scenarios that mirror real-world threats. By providing hands-on experience, employees develop a deeper understanding of cybersecurity principles and learn how to apply them in their daily work routines.
Here’s why cybersecurity awareness training is essential for your organization:
- Reduces Human Error: A significant portion of cyberattacks are initiated through human error. Training helps employees recognize phishing attempts, malware infections, and other common attack vectors, minimizing the risk of accidental breaches.
- Promotes a Culture of Security: By fostering a security-conscious culture, training empowers employees to be active participants in protecting your organization. They become vigilant about data security and report suspicious activities proactively.
- Enhances Compliance: Compliance with data privacy regulations such as GDPR and CCPA requires organizations to demonstrate reasonable security measures. Cybersecurity awareness training contributes to compliance by equipping employees with the knowledge to handle sensitive information responsibly.
- Minimizes Business Disruptions: By reducing the likelihood of successful cyberattacks, training mitigates the potential for business disruptions, data loss, and financial damage.
Investing in cybersecurity awareness training is an investment in the long-term security of your organization. By empowering your workforce to be vigilant and knowledgeable, you create a strong defense against cyber threats, ensuring the safety and resilience of your business in the digital age.
Emerging Cybersecurity Technologies to Watch in 2024
The cybersecurity landscape is constantly evolving, with new threats emerging and attackers becoming more sophisticated. To stay ahead of the curve, businesses must embrace emerging technologies that can enhance their security posture. In 2024, several promising cybersecurity technologies are poised to gain traction and revolutionize how organizations protect themselves. Here are some of the key trends to watch:
Artificial Intelligence (AI) and Machine Learning (ML): AI and ML are rapidly transforming cybersecurity. These technologies can analyze vast amounts of data to identify suspicious activity, predict potential threats, and automate security tasks. AI-powered security solutions can detect anomalies in network traffic, identify phishing attempts, and even respond to threats in real time.
Zero Trust Security: The traditional perimeter-based security model is becoming obsolete as organizations move to the cloud and adopt remote work. Zero trust security assumes that no user or device can be trusted by default, regardless of location. This approach involves verifying every request and user before granting access, reducing the risk of unauthorized access and data breaches.
Extended Detection and Response (XDR): XDR is a modern approach to security that provides a unified view of security events across multiple endpoints, networks, and clouds. By correlating data from various sources, XDR solutions can detect threats faster, respond more effectively, and improve incident response times.
Quantum Computing: Although still in its early stages, quantum computing has the potential to revolutionize cybersecurity. While quantum computers could break existing encryption algorithms, they also offer opportunities for developing new, more secure encryption methods.
Biometric Authentication: Biometric authentication methods, such as facial recognition, fingerprint scanning, and iris scanning, are becoming increasingly popular for securing access to systems and devices. These methods are more secure than traditional passwords and can provide a more convenient user experience.
As cyberattacks become more sophisticated, organizations must embrace these emerging cybersecurity technologies to stay ahead of the curve. By leveraging AI, zero trust, XDR, quantum computing, and biometric authentication, businesses can enhance their security posture and mitigate the risk of cyberattacks.