The world of quantum computing is rapidly advancing, with groundbreaking discoveries happening almost daily. One area that’s particularly exciting is quantum cryptography. This cutting-edge technology promises to revolutionize the way we secure our data, offering unparalleled levels of security that traditional encryption methods simply can’t match.
Imagine a world where your online transactions, private communications, and sensitive data are completely immune to hacking. That’s the potential of quantum cryptography. By harnessing the principles of quantum mechanics, this revolutionary approach can create unbreakable encryption keys, making data theft practically impossible. Join us as we delve into the latest advancements in this field, exploring how quantum cryptography is poised to redefine the future of cybersecurity.
Understanding Quantum Cryptography: A New Era of Security
In the digital age, where information is king, securing data is paramount. As traditional cryptographic methods face increasing vulnerabilities, the emergence of quantum cryptography presents a groundbreaking solution, ushering in a new era of impenetrable security. This innovative approach harnesses the principles of quantum mechanics to create unbreakable encryption keys, rendering data impervious to even the most sophisticated cyberattacks.
Unlike conventional encryption, which relies on complex mathematical algorithms, quantum cryptography leverages the quirky behavior of quantum particles, such as photons. The fundamental principle lies in the inherent uncertainty of quantum states, known as the Heisenberg uncertainty principle. This principle dictates that certain properties of a quantum particle, like its position and momentum, cannot be simultaneously determined with perfect accuracy. By encoding information in the quantum state of these particles, quantum cryptography ensures that any attempt to intercept or eavesdrop on the communication will inevitably alter the state, leaving an unmistakable trace for the legitimate parties to detect.
The inherent tamper-proof nature of quantum cryptography stems from the concept of quantum entanglement. Entangled particles, despite being physically separated, remain interconnected in a way that defies classical understanding. Any measurement performed on one entangled particle instantly affects the state of its entangled counterpart. This phenomenon allows for the creation of secure communication channels where any intrusion is immediately revealed, effectively preventing eavesdropping or manipulation of the data.
While still in its nascent stages, quantum cryptography holds immense promise for transforming the security landscape. Its ability to guarantee secure communication across diverse applications, from financial transactions to sensitive government communications, makes it a transformative force in safeguarding our digital future. As research and development continue, we can expect quantum cryptography to play an increasingly pivotal role in ensuring the integrity and privacy of our digital world.
The Power of Qubits: How Quantum Mechanics Secures Data
In the realm of cybersecurity, the race to stay ahead of ever-evolving threats is constant. Traditional encryption methods, while effective, are increasingly vulnerable to the growing power of quantum computers. This is where quantum cryptography enters the scene, promising a future where data security is unbreakable. At the heart of this revolutionary technology lies the power of qubits.
Unlike classical bits, which can represent either a 0 or a 1, qubits harness the principles of quantum mechanics to exist in a superposition of states, simultaneously representing both 0 and 1. This unique characteristic allows for unprecedented levels of security. Imagine trying to intercept a message encoded using qubits. Any attempt to measure the state of a qubit would inevitably alter it, instantly alerting the sender and rendering the eavesdropping futile.
Quantum key distribution (QKD) is a prime example of how qubits bolster data security. In QKD, a secure key is shared between two parties using entangled pairs of qubits. Any attempt to intercept the key would disrupt the entanglement, revealing the presence of an intruder. This ensures that even if the data itself is compromised, the key used to decrypt it remains secure.
The implications of quantum cryptography are vast. Imagine a future where sensitive financial transactions, medical records, and national security communications are shielded by the unbreakable strength of qubits. The potential to revolutionize cybersecurity is undeniable, marking a new era of digital trust and safeguarding against future threats.
Quantum Key Distribution (QKD): Unbreakable Keys for the Digital Age

In the digital age, security is paramount. As technology advances, so do the threats to our data. Traditional encryption methods, while effective, are vulnerable to evolving hacking techniques. This is where quantum key distribution (QKD) comes in, offering a revolutionary approach to secure communication. QKD leverages the principles of quantum mechanics to create unbreakable keys, ensuring that sensitive information remains protected.
The core of QKD lies in the unique properties of photons, the fundamental particles of light. These photons can be manipulated in ways that are impossible to replicate with classical technology. For example, a single photon can be polarized in different directions, making it possible to create a unique key that can be shared between two parties. Any attempt to intercept or eavesdrop on this key will inevitably alter the quantum state of the photons, leaving a detectable trace. This principle of “quantum entanglement” forms the foundation for secure key distribution.
The implications of QKD are profound. It has the potential to revolutionize secure communication across various sectors. Financial institutions, governments, and even individuals can benefit from the unparalleled security offered by QKD. By using QKD, sensitive data can be transmitted with absolute confidence, knowing that it is protected from even the most sophisticated cyberattacks.
Real-World Applications: Where Quantum Cryptography is Making an Impact
While quantum cryptography remains a relatively new field, its potential for revolutionizing secure communication has captivated researchers and industry leaders alike. This technology, harnessing the principles of quantum mechanics, offers unprecedented levels of security by fundamentally changing how information is encoded and transmitted.
Beyond the theoretical realm, quantum cryptography is already finding its way into real-world applications. Here are some notable examples:
Financial Transactions
Financial institutions are acutely aware of the vulnerabilities inherent in traditional encryption methods. Quantum cryptography provides an extra layer of security for sensitive transactions, ensuring the integrity and confidentiality of financial data. Banks and other financial institutions are exploring the use of quantum key distribution (QKD) to secure online banking, stock trading, and other critical financial activities.
Healthcare Data Protection
The healthcare industry handles sensitive patient data, making it a prime target for cyberattacks. Quantum cryptography can safeguard electronic health records (EHRs) by encrypting them with unbreakable keys. This technology can also secure the transmission of medical images and other critical medical information, enhancing patient privacy and ensuring the integrity of healthcare systems.
Secure Communication Networks
Governments and military organizations rely on secure communication networks to protect national security. Quantum cryptography can be used to build unbreakable communication networks, making it difficult for adversaries to intercept or eavesdrop on sensitive information. This technology is particularly relevant for secure military communications, diplomatic channels, and critical infrastructure protection.
Data Centers and Cloud Security
The increasing reliance on cloud computing has heightened concerns about data security. Quantum cryptography can be employed to protect data stored in data centers and cloud platforms. By leveraging QKD, companies can ensure the confidentiality and integrity of their data, even in the face of advanced cyber threats.
As research and development continue to advance, the applications of quantum cryptography are expected to expand further. This technology has the potential to revolutionize secure communication in various sectors, providing an unprecedented level of protection against future cyber threats.
Overcoming Challenges: Scalability and Implementation of Quantum Cryptography
While quantum cryptography holds immense potential for revolutionizing secure communication, its widespread adoption faces significant hurdles. One major challenge is scalability. Current quantum key distribution (QKD) systems are limited in range and require specialized infrastructure, making them impractical for large-scale deployment.
Another obstacle is implementation. Integrating QKD systems with existing communication networks and protocols poses significant technical difficulties. Moreover, the development of reliable and cost-effective quantum hardware remains a crucial challenge.
To overcome these challenges, researchers are actively pursuing various approaches. These include:
- Developing more robust and efficient QKD protocols
- Improving the performance and scalability of quantum hardware
- Exploring hybrid quantum-classical communication networks
- Developing standardized frameworks for integrating QKD into existing infrastructure
These advancements are paving the way for a future where quantum cryptography becomes a ubiquitous technology, securing sensitive data and communications from evolving cyber threats.
The Future of Cybersecurity: How Quantum Cryptography Will Shape the Digital Landscape
The digital landscape is constantly evolving, and with it, the threats to our online security. As cyberattacks become increasingly sophisticated, traditional methods of encryption are facing a growing challenge. Enter quantum cryptography, a revolutionary technology that promises to revolutionize cybersecurity by leveraging the principles of quantum mechanics.
Quantum cryptography offers unparalleled security by harnessing the fundamental properties of quantum particles. Unlike classical cryptography, which relies on complex mathematical algorithms, quantum cryptography leverages the inherent randomness and uncertainty of quantum states to create unbreakable encryption keys. This means that even with access to the most powerful computers, it would be impossible to crack the encryption without disrupting the quantum state, which would immediately alert the sender and receiver.
The potential applications of quantum cryptography are vast. It can be used to secure everything from financial transactions and confidential communications to critical infrastructure and sensitive data. As we move towards a more interconnected world, where data is constantly flowing, the need for robust and secure communication channels is paramount. Quantum cryptography has the potential to address these challenges and create a more secure digital landscape for the future.
However, the road to widespread adoption of quantum cryptography is not without its challenges. The technology is still in its early stages of development, and there are significant technical hurdles to overcome before it can be implemented on a large scale. Nevertheless, the potential benefits are significant, and ongoing research and development efforts are paving the way for a future where quantum cryptography plays a crucial role in protecting our digital world.
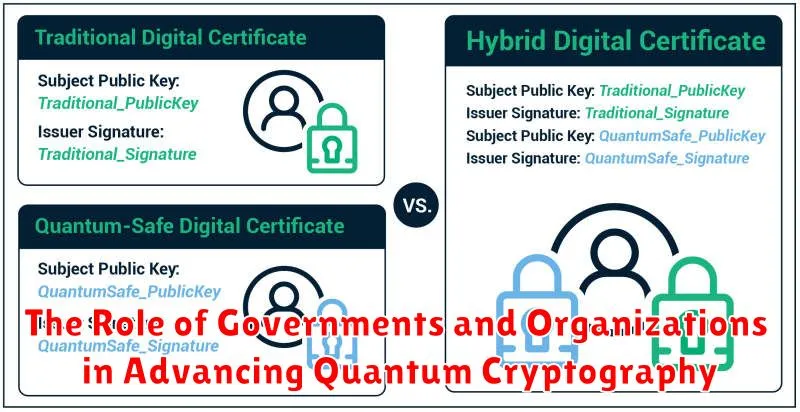
Quantum Cryptography vs. Traditional Cryptography: Understanding the Difference

The world of cybersecurity is constantly evolving, and with the advent of quantum computing, new possibilities for both security threats and defense mechanisms are emerging. One of the most promising developments in this space is quantum cryptography, which leverages the principles of quantum mechanics to create unbreakable encryption systems. But how does it compare to traditional cryptography, and what are the key differences?
Traditional cryptography relies on complex mathematical algorithms to encrypt and decrypt data. These algorithms use keys, which are secret pieces of information that only authorized parties possess. While these methods have proven effective for many years, they are vulnerable to attacks from powerful computers, especially quantum computers.
Quantum cryptography, on the other hand, utilizes the unique properties of quantum mechanics, such as superposition and entanglement, to create fundamentally secure communication channels. Instead of relying on complex mathematical algorithms, it uses the inherent unpredictability of quantum systems to generate random keys. These keys are impossible to intercept or copy without altering the quantum state, making it virtually impossible for eavesdroppers to gain access to the information. This makes it significantly more robust against attacks from traditional and quantum computers.
Here’s a table summarizing the key differences between traditional and quantum cryptography:
| Feature | Traditional Cryptography | Quantum Cryptography |
|---|---|---|
| Encryption Method | Mathematical algorithms | Quantum mechanics principles |
| Key Generation | Random number generators | Quantum phenomena (superposition, entanglement) |
| Security | Vulnerable to attacks by powerful computers, including quantum computers | Unbreakable, as eavesdropping alters the quantum state |
While still in its early stages, quantum cryptography holds the potential to revolutionize secure communication. Its ability to withstand attacks from even the most advanced computers makes it a crucial tool for safeguarding sensitive information in the age of quantum computing. As quantum technologies continue to advance, we can expect to see further breakthroughs in this field, leading to even more secure and reliable communication systems in the future.
Quantum Hacking: Threats and Countermeasures in a Quantum World
As quantum computing advances, it brings unprecedented computational power, but it also introduces new threats to our digital security. Quantum hacking leverages the principles of quantum mechanics to crack cryptographic algorithms that are currently considered secure. This poses a significant threat to our existing cybersecurity infrastructure, including online banking, digital communications, and sensitive data storage.
One of the most concerning threats is the ability of quantum computers to break public-key cryptography, a cornerstone of modern encryption. Algorithms like RSA and ECC, which rely on the difficulty of factoring large numbers or finding discrete logarithms, are vulnerable to attacks from sufficiently powerful quantum computers. This could compromise the security of online transactions, sensitive data, and even national security communications.
Fortunately, the field of quantum cryptography is developing countermeasures to address these threats. Quantum key distribution (QKD) is a promising solution that uses the principles of quantum mechanics to establish a secure communication channel between two parties. QKD ensures that any eavesdropping attempt will be detected, guaranteeing the security of the exchanged key.
Another promising approach is post-quantum cryptography (PQC), which focuses on developing new cryptographic algorithms that are resistant to quantum attacks. These algorithms rely on mathematical problems that are considered computationally difficult even for quantum computers. PQC is being actively researched and standardized by organizations like NIST, and it has the potential to replace current cryptographic algorithms.
The future of cybersecurity in the quantum era requires a proactive approach. It is crucial to invest in research and development of quantum cryptography and PQC to ensure the resilience of our digital infrastructure. Governments, industry leaders, and researchers must collaborate to develop robust countermeasures against quantum hacking and secure our future in a quantum world.
Quantum-Resistant Algorithms: Preparing for the Post-Quantum Era

The advent of quantum computing presents both exciting opportunities and significant challenges. One of the most pressing concerns is the threat it poses to modern cryptography, which relies on mathematical problems that can be easily broken by quantum computers. To address this, researchers are actively developing quantum-resistant algorithms, also known as post-quantum cryptography, which are designed to withstand attacks from even the most powerful quantum computers.
These algorithms rely on different mathematical principles compared to traditional cryptography. They leverage problems that remain difficult even for quantum computers, such as the hardness of finding short vectors in lattices or solving certain types of equations. Several promising candidates for quantum-resistant algorithms have emerged in recent years, including:
- Lattice-based cryptography: This approach relies on the difficulty of finding short vectors in high-dimensional lattices.
- Code-based cryptography: This method leverages the complexity of decoding error-correcting codes.
- Multivariate cryptography: This technique uses the difficulty of solving systems of multivariate polynomial equations.
- Isogeny-based cryptography: This approach exploits the properties of elliptic curves and their isogenies.
- Hash-based cryptography: This method relies on the security of cryptographic hash functions.
These algorithms are still under active research and development, but significant progress has been made. Standardization efforts are underway to ensure the widespread adoption and interoperability of these technologies. Governments and organizations around the world are investing heavily in post-quantum cryptography research, recognizing its crucial role in safeguarding our digital infrastructure in the post-quantum era.
The development and deployment of quantum-resistant algorithms are crucial for ensuring the continued security of our digital world. As quantum computing technology advances, it is essential to stay ahead of the curve and prepare for the post-quantum future.
Investing in Quantum Security: Why Businesses Need to Pay Attention
The emergence of quantum computing poses a significant threat to the cybersecurity landscape, as its processing power can potentially break current encryption methods. This impending threat has fueled the development of quantum-resistant cryptography, also known as post-quantum cryptography, a crucial step towards safeguarding our digital world. As we navigate this evolving technological landscape, businesses must prioritize investing in quantum security to ensure the resilience of their data and systems.
Quantum computers, with their ability to perform calculations at an unprecedented speed, can crack the encryption algorithms that currently protect sensitive data. This capability poses a serious risk to businesses, jeopardizing sensitive information like financial records, customer data, and intellectual property. Therefore, proactively investing in quantum-resistant cryptography is crucial to prevent potential breaches and maintain the integrity of digital assets.
Investing in quantum security is not just a reactive measure; it’s a proactive approach to securing the future. By adopting quantum-resistant algorithms, businesses can future-proof their cybersecurity infrastructure and minimize the risk of vulnerability to quantum attacks. Furthermore, investing in quantum security demonstrates a commitment to responsible data management, building trust with customers and partners.
While quantum computers are still in their early stages of development, the threat they pose is real and imminent. Businesses must act now to implement quantum-resistant cryptography, ensuring that their data and operations are protected from the potential vulnerabilities of the quantum era.
The Role of Governments and Organizations in Advancing Quantum Cryptography
The rapid development of quantum cryptography is driven not only by scientific advancements but also by the proactive role of governments and organizations worldwide. These entities are vital in fostering innovation, setting standards, and ensuring the safe and responsible implementation of this transformative technology. Governments play a critical role in providing funding and research grants to support the development of quantum cryptography technologies. By investing in research institutions, universities, and private companies, governments are accelerating the pace of scientific discovery and the transition of quantum cryptography from the laboratory to real-world applications.
Furthermore, governments are establishing regulatory frameworks and security protocols to guide the deployment and usage of quantum cryptography. This is crucial in building public trust and confidence in the security of communication networks that utilize quantum cryptography. Organizations, including industry consortia, research institutions, and standard-setting bodies, are also playing a vital role. They collaborate on developing industry standards, interoperability protocols, and best practices for implementing quantum cryptography across different platforms and systems.
These organizations are also actively working to educate the public and the industry about the potential of quantum cryptography and its implications for cybersecurity. By fostering collaboration and knowledge sharing, they are empowering businesses and individuals to make informed decisions about adopting this transformative technology. The combined efforts of governments and organizations are essential in unlocking the full potential of quantum cryptography and ensuring its responsible and secure integration into the digital landscape.

