In the digital age, where data is constantly flowing through networks, safeguarding sensitive information is paramount. Data encryption has emerged as an indispensable tool for bolstering cybersecurity, ensuring the confidentiality and integrity of your digital assets. But with a plethora of encryption technologies available, navigating the complexities of this field can be daunting. This article aims to demystify the world of unbreakable codes, shedding light on the diverse encryption methods employed to protect your data and empower you to make informed security decisions.
From the seemingly simple symmetric-key encryption to the sophisticated asymmetric-key encryption, we will delve into the inner workings of these methods, exploring their strengths, weaknesses, and real-world applications. We will also examine the latest advancements in quantum-resistant encryption, a promising technology designed to withstand the threat posed by powerful quantum computers. By understanding the nuances of data encryption, you can gain a deeper appreciation for the crucial role it plays in safeguarding your digital life and building a more secure future.
The Importance of Data Encryption in the Digital Age
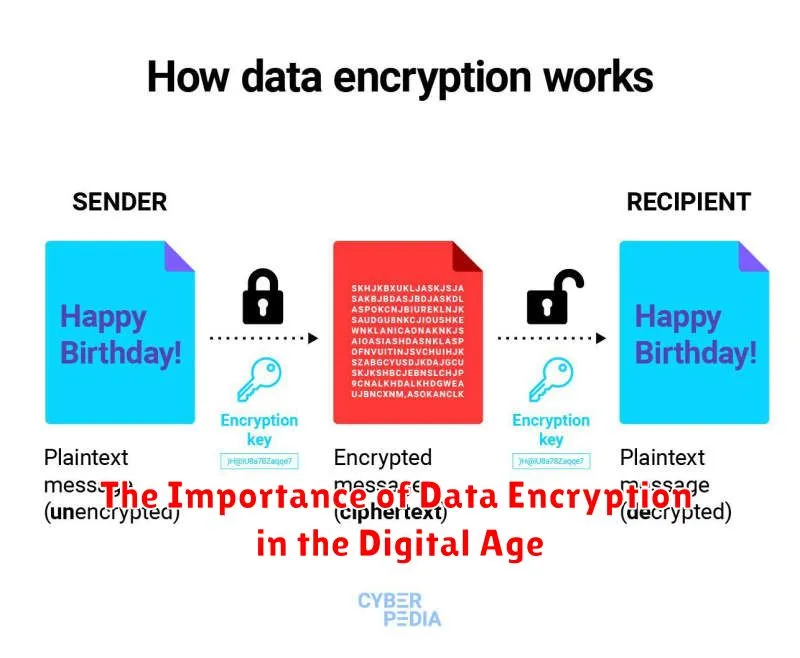
In the digital age, where information is constantly being transmitted and stored online, the importance of data encryption cannot be overstated. Data encryption is a crucial security measure that transforms data into an unreadable format, ensuring its confidentiality and integrity. This is essential for protecting sensitive information from unauthorized access, interception, or modification.
As we increasingly rely on technology for everything from banking and shopping to communication and healthcare, the threat of cyberattacks is ever-present. Data breaches can have devastating consequences, leading to financial losses, identity theft, and reputational damage. By employing strong encryption methods, organizations and individuals can significantly reduce the risk of these attacks and safeguard their valuable data.
Encryption works by using algorithms and keys to transform plain text into ciphertext, which is unintelligible without the corresponding decryption key. This makes it incredibly difficult for hackers to access or understand the encrypted data, even if they manage to intercept it.
The benefits of data encryption are numerous. It helps to ensure:
- Confidentiality: Only authorized individuals with the correct decryption key can access the data.
- Integrity: Encryption safeguards data from unauthorized modifications, guaranteeing its authenticity.
- Compliance: Many industries and regulations require data encryption to protect sensitive information, such as healthcare data and financial records.
In today’s interconnected world, data encryption is not just a luxury but a necessity. By understanding and implementing robust encryption solutions, we can create a safer and more secure digital environment for everyone.
Symmetric Encryption: A Single Key for Simplicity
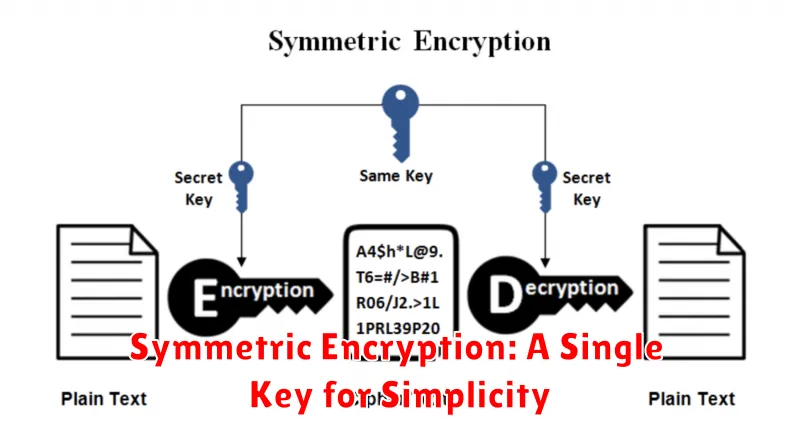
In the realm of data security, encryption plays a vital role in safeguarding sensitive information. Among various encryption techniques, symmetric encryption stands out for its simplicity and efficiency. This method employs a single key for both encrypting and decrypting data, making it a straightforward approach to securing sensitive information.
Imagine a lock and key mechanism. In symmetric encryption, the same key unlocks the data (decryption) as the one used to lock it (encryption). This shared key is kept secret between the sender and receiver, ensuring that only authorized parties can access the encrypted information. This simplicity makes symmetric encryption a popular choice for various applications, including:
- File Encryption: Protecting sensitive documents, spreadsheets, and other files.
- Database Encryption: Securing data stored in databases, ensuring privacy and integrity.
- Network Security: Encrypting communication over networks, safeguarding data transmission.
The simplicity of symmetric encryption is its strength. With only one key to manage, it reduces complexity and enhances ease of use. However, it’s crucial to remember that the security of symmetric encryption hinges on keeping the key secret. If the key is compromised, the entire system is vulnerable. This highlights the importance of strong key management practices to maintain the integrity of the encryption process.
Asymmetric Encryption: Public and Private Keys Explained
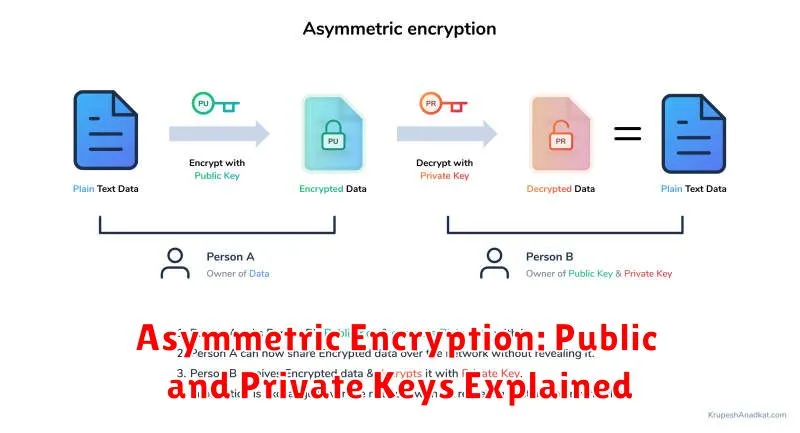
In the realm of data security, encryption stands as a stalwart guardian, safeguarding sensitive information from unauthorized access. Among the various encryption methods, asymmetric encryption, also known as public-key cryptography, reigns supreme with its unique approach to key management.
Unlike symmetric encryption, where the same key is used for both encryption and decryption, asymmetric encryption employs two distinct keys: a public key and a private key.
The public key, as its name suggests, is freely available to anyone who wishes to send encrypted messages. This key can only encrypt data; it cannot decrypt it. Conversely, the private key remains a closely guarded secret, known only to the intended recipient. This key can decrypt data encrypted with the corresponding public key.
The beauty of asymmetric encryption lies in its ability to establish secure communication without the need to share a secret key. Anyone can use the public key to encrypt a message, but only the holder of the private key can decrypt it. This eliminates the risk of key compromise, making it a robust solution for sensitive data protection.
Here’s an analogy to understand this concept: Imagine a mailbox with two slots. The public key is like the public slot where anyone can drop a letter (encrypted message). The private key is the private slot inside the mailbox where only the owner can retrieve the letter (decrypt the message).
Asymmetric encryption finds widespread applications in various domains:
- Secure email communication: Emails encrypted using public-key cryptography ensure that only the intended recipient can read the message.
- Digital signatures: Private keys are used to generate digital signatures, ensuring the authenticity and integrity of electronic documents.
- Secure website authentication: Websites use SSL/TLS certificates based on asymmetric encryption to establish secure connections with users, protecting sensitive information like passwords and credit card details.
- Cryptocurrency transactions: Public-key cryptography plays a crucial role in securing cryptocurrency transactions, ensuring that only the rightful owner can access and spend their funds.
In conclusion, asymmetric encryption stands as a cornerstone of modern security, empowering us to safeguard sensitive information in a world where data breaches are ever-present. Its unique approach to key management, with its distinct public and private keys, ensures robust security and privacy, paving the way for a more secure digital future.
Hashing Algorithms: Ensuring Data Integrity
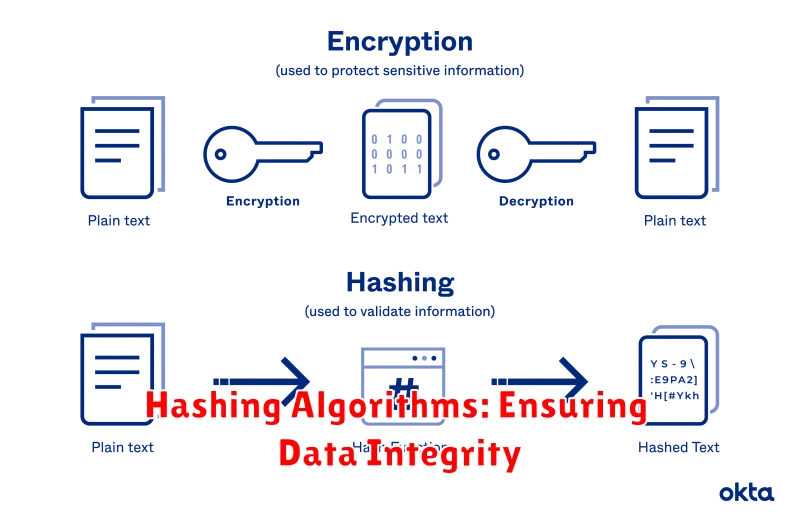
In the realm of cybersecurity, ensuring data integrity is paramount. This means guaranteeing that data remains unaltered and authentic, safeguarding it from malicious modifications. Hashing algorithms play a pivotal role in achieving this goal.
A hashing algorithm takes an input, known as the “message,” and transforms it into a fixed-size string of characters called a “hash.” This hash acts as a unique fingerprint, representing the original message. Any changes made to the message, no matter how subtle, will result in a completely different hash.
The key principle behind hashing algorithms is their one-way nature. While it’s easy to generate a hash from a message, it’s practically impossible to reverse the process and retrieve the original message from its hash. This makes hashing algorithms incredibly valuable for verifying data integrity.
Here’s how hashing algorithms ensure data integrity:
- Data Verification: When a file or message is received, its hash can be calculated and compared to the original hash. If they match, it confirms that the data has not been tampered with. This is particularly crucial for downloading files from the internet.
- Password Security: Instead of storing passwords in plain text, hashing algorithms are used to transform them into secure hashes. This prevents unauthorized access even if a database is compromised.
- Digital Signatures: Hashing algorithms are essential for creating digital signatures, which verify the authenticity of digital documents. By applying a hash to a document and then signing it with a private key, recipients can ensure the document’s origin and integrity.
Commonly used hashing algorithms include MD5, SHA-1, and SHA-256. While these algorithms are effective, it’s important to note that they are not unbreakable. Over time, advances in computing power can compromise their security. Therefore, it’s crucial to stay updated on the latest recommendations and use robust algorithms.
Advanced Encryption Standard (AES): The Gold Standard
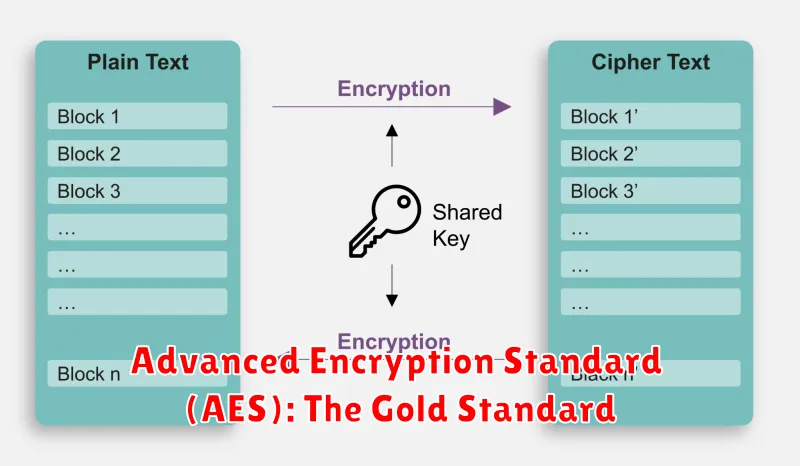
In the realm of cybersecurity, the term “unbreakable” is often thrown around, but the reality is that no encryption algorithm is truly impervious to attack. However, one algorithm stands head and shoulders above the rest in terms of its strength and widespread adoption: the Advanced Encryption Standard (AES).
Adopted by the US government in 2001, AES is a symmetric-key block cipher, meaning it uses the same key for both encryption and decryption. This key is a string of bits, and its length determines the complexity of cracking the encryption. AES offers three key lengths: 128, 192, and 256 bits, with the longer key offering greater security.
The strength of AES lies in its intricate design. It employs a series of mathematical operations, including substitution, permutation, and mixing, to transform plaintext data into an unintelligible ciphertext. This process is highly complex, making it extremely difficult for attackers to decipher the encrypted data without the correct key.
AES has earned its reputation as the “gold standard” for several reasons. First, its robustness has been extensively tested and analyzed by the cryptographic community, with no significant weaknesses discovered. Second, its widespread adoption in various applications, including web browsers, operating systems, and even hardware encryption, makes it the de facto standard for secure data transmission and storage.
However, it’s crucial to note that even AES is not immune to vulnerabilities. Improper implementation, weak key management, or other security flaws can compromise its effectiveness. Therefore, proper cryptographic practices and secure key handling are essential for leveraging the full potential of AES.
In conclusion, the Advanced Encryption Standard (AES) is a highly secure and widely adopted encryption algorithm that plays a critical role in safeguarding sensitive information. While not “unbreakable” in the absolute sense, its robust design and broad adoption make it the gold standard for protecting data in the digital age.
Data Encryption Standard (DES) and Triple DES
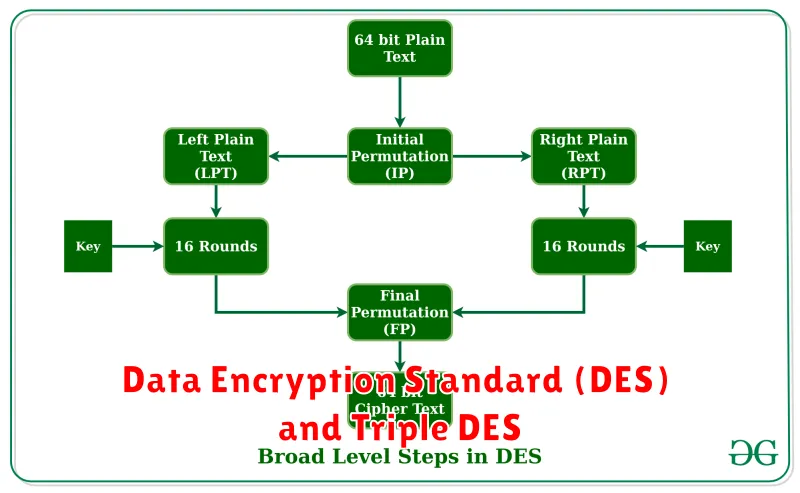
In the realm of cybersecurity, data encryption plays a pivotal role in safeguarding sensitive information. Among the early encryption standards that gained widespread adoption was the Data Encryption Standard (DES). Developed in the 1970s, DES utilized a symmetric-key algorithm, meaning the same key was used for both encryption and decryption. The algorithm employed a 56-bit key to encrypt data in blocks of 64 bits, making it computationally intensive for brute-force attacks at the time.
However, as technology advanced, the 56-bit key length of DES became vulnerable to brute-force attacks, prompting the development of Triple DES (3DES). This enhanced encryption standard essentially applied the DES algorithm three times, using three different keys. This resulted in a much larger effective key length of 168 bits, making it significantly more secure than its predecessor.
While Triple DES offered a significant improvement in security, it was eventually superseded by more modern encryption algorithms like Advanced Encryption Standard (AES). AES employs a 128-bit block size and key lengths of 128, 192, or 256 bits, offering even greater security against attacks. Despite their historical significance, DES and Triple DES are no longer considered secure for most applications. Their legacy, however, remains as foundational components in the evolution of modern encryption technologies.
Rivest-Shamir-Adleman (RSA) Encryption

In the digital realm, where information flows freely, ensuring the security of sensitive data is paramount. Rivest-Shamir-Adleman (RSA) encryption, named after its inventors, stands as a cornerstone of modern cryptography, safeguarding our online transactions, communications, and digital identities. This powerful algorithm utilizes asymmetric cryptography, meaning it employs separate keys for encryption and decryption, adding a layer of complexity that makes it incredibly difficult to crack.
At its core, RSA revolves around the concept of prime factorization. It generates two large prime numbers, multiplying them to obtain a public key. This public key is shared openly, while the prime numbers themselves remain secret, forming the private key. The beauty of RSA lies in the mathematical challenge of factoring large numbers. While it’s easy to multiply primes, factoring them back into their original components is computationally intensive, even for the most powerful computers. This difficulty forms the basis of RSA’s security.
To encrypt data, a sender uses the recipient’s public key. Decryption, however, requires the corresponding private key, held only by the intended recipient. This one-way nature of RSA makes it ideal for digital signatures, ensuring message authenticity and non-repudiation. Think of it like a digital seal, guaranteeing the message’s origin and integrity.
Despite its robustness, RSA is not invulnerable. As computing power advances, the size of prime numbers needed to maintain security increases. Additionally, potential vulnerabilities arise from poor key management practices and weak random number generators. Therefore, proper implementation and ongoing vigilance are crucial to harnessing the full potential of RSA for secure data exchange.
In conclusion, RSA encryption remains a powerful tool for safeguarding sensitive information. Its reliance on complex mathematical principles and asymmetric key pairs makes it a formidable barrier against unauthorized access. As we navigate the ever-evolving landscape of cybersecurity, understanding RSA’s strengths and limitations is essential for building robust and resilient digital defenses.
Blowfish and Twofish Encryption Algorithms
In the realm of data security, robust encryption algorithms are paramount. Blowfish and Twofish are two prominent symmetric-key block ciphers, known for their efficiency and security, playing crucial roles in protecting sensitive information. Let’s delve into the intricacies of these algorithms and understand their significance in the world of data encryption.
Blowfish: A Legacy of Strength
Designed by Bruce Schneier in 1993, Blowfish is a fast, versatile block cipher with a variable key length, making it adaptable to various security requirements. Its key strength lies in its complex key scheduling algorithm, which generates subkeys from the user-provided key, creating a highly secure and unpredictable encryption process. Blowfish operates on 64-bit blocks of data, iterating through a series of operations including XOR, S-box lookups, and additions, resulting in a highly secure encrypted output.
Twofish: An Evolution in Security
Twofish, also developed by Bruce Schneier and his team, is a more advanced block cipher that builds upon the principles of Blowfish. It boasts a larger block size of 128 bits, offering greater security and resistance against modern cryptanalytic attacks. The key scheduling algorithm in Twofish is even more complex, incorporating a variety of cryptographic operations to generate a secure keystream. Furthermore, Twofish employs a 16-round Feistel network, making it significantly more robust against brute-force attacks.
Applications of Blowfish and Twofish
Both Blowfish and Twofish have found widespread use in various applications, including:
- File and disk encryption
- Database security
- Secure communication protocols
- Network security
Conclusion
Blowfish and Twofish are highly regarded encryption algorithms that have earned their reputation for strength and efficiency. Their adoption in various applications underlines their critical role in protecting sensitive data from unauthorized access. As the landscape of cyber threats continues to evolve, these algorithms remain valuable tools in the ongoing fight for data security.
Elliptic Curve Cryptography (ECC)
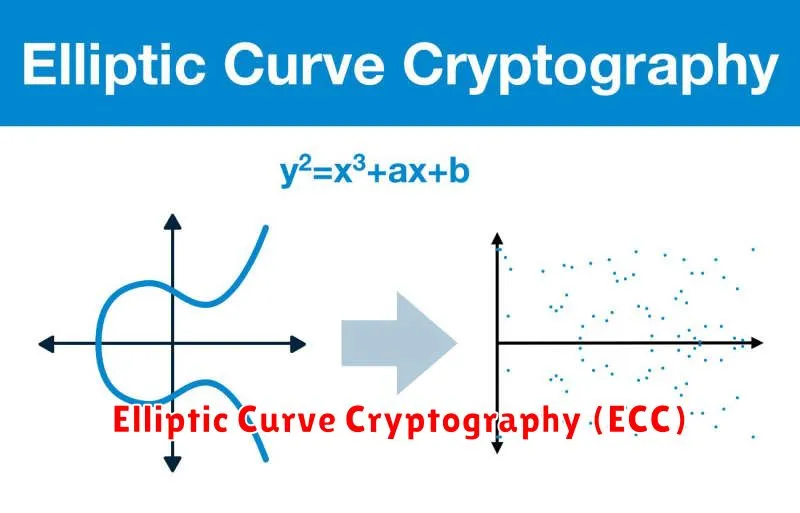
In the ever-evolving landscape of cybersecurity, robust encryption methods are paramount for safeguarding sensitive data. Among the leading contenders, Elliptic Curve Cryptography (ECC) stands out as a modern and efficient technique for secure communication. Unlike traditional encryption algorithms like RSA, ECC leverages the mathematical properties of elliptic curves to create strong cryptographic keys.
At its core, ECC relies on the concept of points on an elliptic curve, where the coordinates of these points represent cryptographic keys. The beauty of ECC lies in its ability to generate strong keys with shorter lengths compared to traditional algorithms. This translates into faster encryption and decryption processes, especially crucial for resource-constrained devices like smartphones and embedded systems.
ECC offers several compelling advantages:
- Enhanced Security: ECC provides a higher level of security with shorter key lengths, making it resistant to brute-force attacks.
- Improved Performance: Due to shorter key lengths, ECC offers faster encryption and decryption speeds, enhancing efficiency.
- Scalability: ECC is well-suited for handling large-scale data encryption tasks, particularly in cloud environments.
ECC is now widely adopted across various industries, including:
- Financial institutions: Securing online banking transactions and digital payments.
- E-commerce: Protecting sensitive customer information during online purchases.
- Mobile devices: Ensuring secure communication and data protection on smartphones and tablets.
As the threat landscape continues to evolve, ECC’s strengths make it a critical component in safeguarding our digital world. Its combination of security, efficiency, and scalability positions it as a cornerstone of modern cryptography.
Homomorphic Encryption: Computing on Encrypted Data
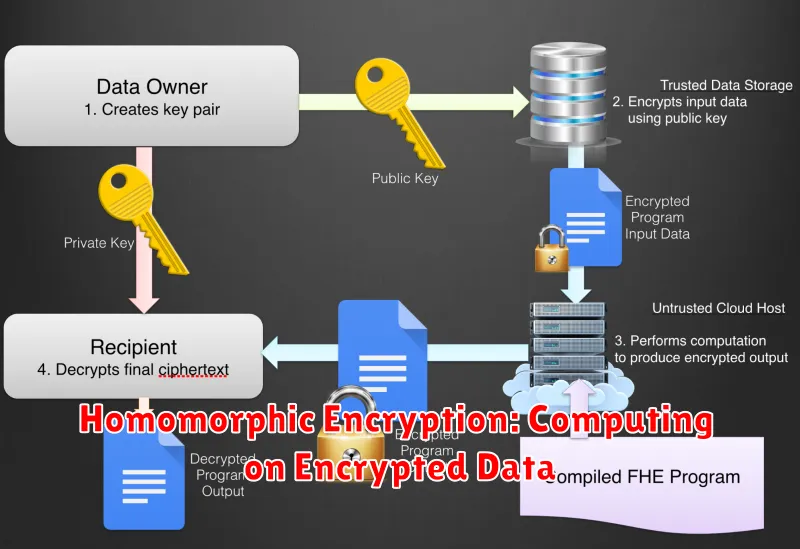
Imagine a world where you can perform calculations on encrypted data without ever decrypting it. This seemingly impossible feat is achievable with homomorphic encryption, a revolutionary encryption technique that allows computations on encrypted data, producing an encrypted result that can be decrypted to reveal the outcome of the computation. This unlocks a realm of possibilities for secure data processing, particularly in areas where privacy and confidentiality are paramount.
The core concept behind homomorphic encryption revolves around the ability to perform operations directly on encrypted data. Unlike traditional encryption methods where decryption is required before any computations, homomorphic encryption allows computations to be carried out on ciphertext, resulting in an encrypted output. This output, when decrypted, reveals the result of the computation as if it were performed on the original, unencrypted data.
Homomorphic encryption is not without its challenges. The complexity of the algorithms involved can lead to significant performance overhead, and the computational demands can be substantial. Nonetheless, advancements in research and development are continuously addressing these limitations, pushing the boundaries of what is possible with secure data processing.
The potential applications of homomorphic encryption are vast and diverse. In healthcare, it can enable secure analysis of sensitive patient data without compromising privacy. In finance, it can facilitate secure financial transactions and data analysis while protecting sensitive financial information. And in cloud computing, it can enable secure data processing and storage in the cloud, without compromising the confidentiality of the data.
As the field of homomorphic encryption continues to evolve, we can anticipate even more innovative applications emerging. This breakthrough technology holds the key to unlocking a future where secure data processing is not a limiting factor but a foundational principle, paving the way for a more secure and privacy-conscious digital world.
Choosing the Right Encryption Method
In the ever-evolving digital landscape, safeguarding sensitive data has become paramount. Encryption, the process of transforming data into an unreadable format, plays a pivotal role in protecting information from unauthorized access. With numerous encryption methods available, choosing the right one is crucial to ensure optimal security.
The selection of an encryption method depends on various factors, including the nature of the data, the level of security required, and the computational resources available.
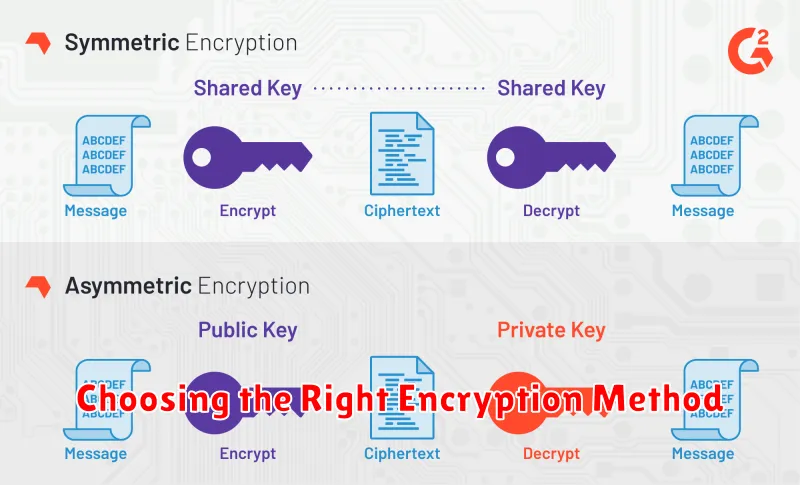
Symmetric Encryption: In symmetric encryption, the same key is used for both encryption and decryption. This method is generally faster than asymmetric encryption but requires secure key distribution. Popular examples include Advanced Encryption Standard (AES) and Triple DES (3DES).
Asymmetric Encryption: Asymmetric encryption utilizes separate keys for encryption and decryption. This approach offers better key management and is commonly used for digital signatures and secure communication. Widely known algorithms include RSA and Elliptic Curve Cryptography (ECC).
Hashing: Hashing algorithms convert data into a fixed-length hash value. While not strictly encryption, hashing is valuable for data integrity verification. Popular algorithms include MD5 and SHA-256.
Choosing the Right Method: Consider these factors when selecting an encryption method:
- Data Sensitivity: Highly sensitive data requires strong encryption algorithms like AES-256.
- Performance Requirements: Encryption can impact system performance. Choose algorithms that strike a balance between security and speed.
- Compliance Standards: Comply with industry regulations and best practices when selecting encryption methods.
Choosing the right encryption method is crucial for bolstering data security. By carefully evaluating factors such as data sensitivity, performance requirements, and compliance standards, you can select an encryption solution that effectively protects your valuable information.

